[ad_1]
I’m not a tinfoil conspiracy theorist by any means, but smartphone data privacy has been on my mind for quite some time. You can never be sure enough when it comes to data security and privacy, and there’s no better single source of information on anyone’s online (and to an extent, offline) life than their smartphone.
Look, I’m not carrying state secrets, nor am I influential enough to topple governments, but I don’t like the idea of someone having access to my data without my knowledge. While online, I follow all the usual safety precautions like using a VPN, ad and tracker blockers on Android and Chrome, and more. However, there’s one element of the puzzle that remains a wildcard. What if someone had access to my phone? Or worse, what if someone could pull the data off my phone after I’d factory reset it and sold it off? Hollywood crime thrillers certainly make it seem easy enough.
Here’s the thing: running a factory reset on your Android phone is usually enough security for most, but is it enough to thwart the most dog-headed of hackers, or umm… governments? Okay, conspiracy theories aside, I promise you I’m not being paranoid. I know the chances that anyone will bother taking my phone into a million-dollar clean room facility are negligible. However, as a child of the 90s, security hygiene has been drilled into my head. For example, I run a nail gun through a hard drive that’s being discarded and zero out old flash drives or SSDs before tossing them out.
You can never be too cautious when it comes to your data and, lately, I’ve been following the same philosophy towards securely erasing the data on my phone when upgrading to a new Android phone or passing it down to a relative.
Can data be recovered after a factory reset on an Android phone?

Edgar Cervantes / Android Authority
The short answer to that is no. The slightly longer answer? Probably not. While social engineering and key loggers remain the most common way of getting into your phone, extracting data from your device is not impossible — even after a factory reset.
All modern phones ship with encryption enabled out of the box, and adding a complex passcode to the lock screen is all it takes to add a serious amount of security. However, it’s a popular misconception that encryption and security are a guarantee against data theft. Even the most advanced security is really just a deterrent to the point where the amount of resources it takes to break through is too high for most hackers to deploy. Think of it like a fortified wall around your home — you can build it high enough, but someone with a tall enough ladder can still climb over it.
Security is like a fortified wall around your home — you can build it high enough, but someone with a tall enough ladder can still climb over it.
Modern Android phones use a type of encryption called file-based encryption. Rolled out starting Android 9.0, file-based encryption protects files in the user data partition, and system partition separately. Each file is independently encrypted using a unique key. In fact, all user data is protected by keys that are generated using a combination of hardware-specific keys and user credentials like, say, a pin or gesture-based unlock. Meanwhile, since the system partition is secured using device-specific keys, file-based encryption will let your phone boot, as usual, all the way through to the lock screen. This means you can receive phone calls or activate alarms even without logging in. Give it a shot: If you restart your phone and don’t enter your PIN, any phone call received will not display the associated contact details. That’s file-based encryption at play, keeping your personal data safe.
However, secure as it is, there’s no such thing as fully secure in the world of computing, and file-based encryption on Android has been broken in the past. While recovering the master key from RAM requires literal surgery on a smartphone, it’s not outside the realm of possibility for a dedicated enough person and has been achieved. Successful attempts have also been made at hacking into Samsung’s secure enclave chip to take the phone from the BFU (Before First Unlock) to AFU (After First Unlock) stage, which decrypts the user partition and makes it a cinch to dump files.
Recovering data from a reset Android device is technically possible, but highly challenging, making the average user an unlikely victim.
Assuming you’ve reset your phone already, it gets more complicated. Since the encryption key is tied to your password, the phone automatically resets the key after a factory reset. A savvy hacker can still dump the phone’s storage, perform data forensics on it, and extract files. However, those files would still be encrypted, and reading them is next to impossible. In fact, Android uses AES-256 standard encryption, which, as of today, remains unbroken. So, yes, your data can be recovered, but it would be unreadable.
However, established tools like Cellebrite, marketed to security agencies and governments, are known to have additional exploits to break through the security on your phone and extract information. Cellebrite advertises that it can access both BFU and AFU modes, decrypt third-party data, and even extract a phone’s complete file system for further data analysis. Considering that Cellebrite can break through BFU and AFU encryption, it’s not out of the realm of possibility that it can generate decryption keys for existing data too.
That said, as I mentioned earlier, you’ve probably got more significant problems to worry about if the government is trying to hack into your phone. For most users, a standard system reset should suffice.
How to completely wipe an Android phone before selling it
Dhruv Bhutani / Android Authority
If you’ve made it so far, you might be thinking that there’s absolutely no need for you to worry about your data being stolen once you’ve factory reset your phone. While that statement is largely true, taking additional measures to secure your data is never a bad idea. Information security is preventative by nature, and ensuring that your private data has been securely wiped is an easy and essential step towards guaranteeing it.
The old-school method of writing gibberish binary data on storage is still the most effective at ensuring that your data is unreadable.
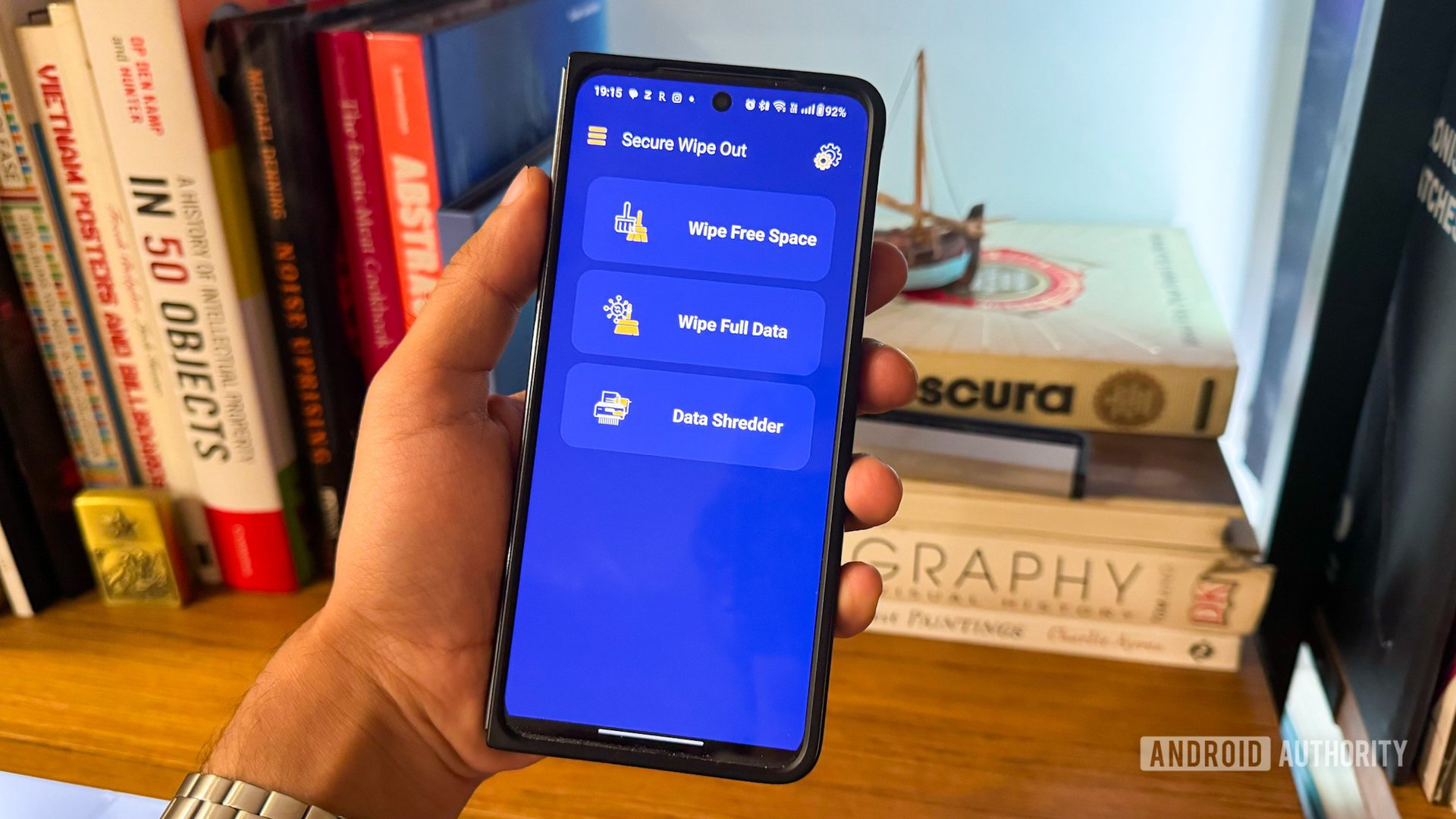
As it turns out, the solution is pretty simple and the same as what we’ve used for decades to secure hard drives. Zeroing out the storage on your phone is a sure-shot way of guaranteeing that it would be gibberish even if someone manages to extract data from your phone. The Android Play Store has several apps that can perform the task, but I’ve had good luck with the Secure Wipe Out app to perform several runs of writing large-scale binary data to the NAND.
While a standard file deletion just marks a particular file as deleted, it generally stays on the disk until another file is written over it. Writing tens or hundreds of gigabytes of non-sensical zero and one binary data on the phone’s storage guarantees that any remaining personal data on your phone’s storage gets overwritten. The process can take a few hours if you’ve got a significant amount of storage on your phone, but it guarantees that your phone has been securely erased and is worth it for the peace of mind it offers. Of course, you should still factory reset your phone after wiping it clean.
So, is it enough to just factory reset your Android phone before selling it?
Edgar Cervantes / Android Authority
While it’s unlikely that almost anyone reading this article would be a potential target for such an attack, it’s always a good idea to take precautionary measures to protect your data on the off-chance someone decides to go rogue with your phone. A factory reset on a modern Android phone is very effective at protecting you from data theft. However, I believe that erring towards caution and running a secure wipe program for a few hours before turning your phone in for an upgrade to a hot upcoming Android phone is a small price to pay for guaranteeing that your personal data remains personal.
Yes, it is possible to remotely wipe an Android phone using the Find My Device utility. Head on over to android.com/find and sign in to your Google account. Select the lost device, and select the erase phone option. This will permanently delete all data on the phone as long as it is connected to the internet.
The Android factory reset turns off Find My Device and you will no longer be able to locate your phone.
While you cannot recover photos from the phone after a factory reset, as long as you have backups enabled in Google Photos, your photos should safely be in the cloud.
Yes, it is possible to factory reset an Android phone without a password using the recovery menu. Press and hold the power button and volume down button for ten seconds. This will restart your phone and boot you into recovery mode. Navigate the recovery mode using the volume buttons, and select the wipe data option. This will factory reset your Android phone.
[ad_2]