[ad_1]
In context: Dynamic voltage and frequency scaling (DVFS) is a technique adopted by modern CPUs and graphics chips to manage power and speed, adjusting frequency and voltage “on the fly” to reduce energy consumption and heat generation. With a “Hot Pixels” attack, DVFS becomes yet another channel a (very) resourceful attacker could exploit to steal data and compromise user’s privacy.
Hot Pixels is a new side-channel attack conceived by an international team of researchersposing a theoretical security threat that exploits Dynamic Voltage and Frequency Scaling (DVFS) techniques to “probe analog properties” of computing devices. DVFS is essential in maintaining a delicate balance between power consumption, heat dissipation, and execution speed (i.e., frequency), the researchers explain in their paper. However, it also introduces software-visible hybrid side-channels through which sensitive data can be extracted.
The researchers targeted Arm-based SoC units, Intel CPUs, and discrete GPUs manufactured by AMD and Nvidia, as these are the most prevalent microchips currently available in the market. A side-channel attack is an attack that leverages residual information, which can be extracted due to the inherent operational nature of a computer component, rather than by exploiting specific security flaws in the design.
The team examined the vulnerability of the aforementioned computing devices to information leakage via power, temperature, and frequency values, which can be conveniently read on a local system thanks to the internal sensors embedded in the chips themselves. No admin access is necessary in this case: the data is persistently available, and DVFS values can be manipulated to operate as constants to assist in identifying specific instructions and operations.
In their experiments with DVFS readings, the researchers discovered that passively-cooled processors (like Arm chips used in smartphones) can leak information via power and frequency readings. Conversely, actively-cooled processors, such as desktop CPUs and GPUs, can leak information through temperature and power readings.
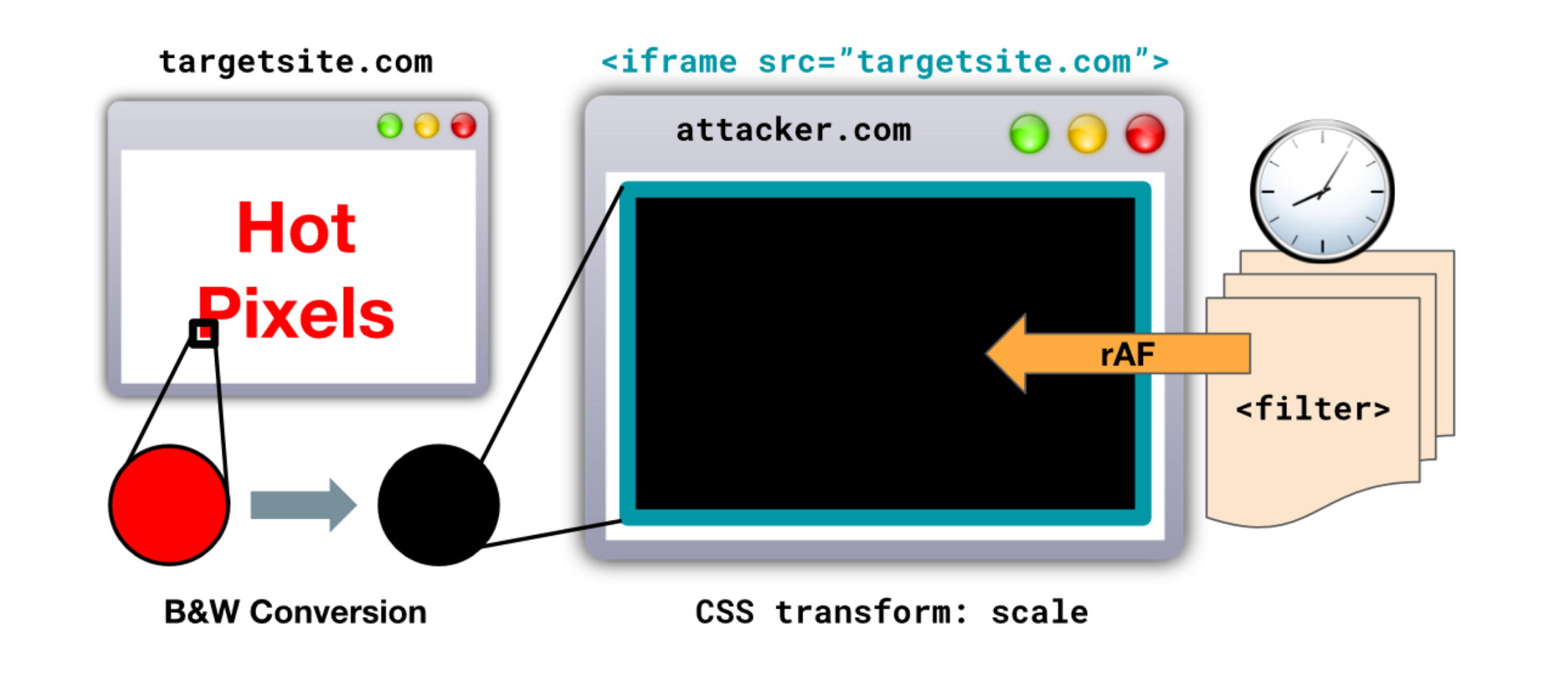
The “Hot Pixels” attacks were thus designed as a practical demonstration of the DVFS-related issue. This includes a JavaScript-based pixel stealing proof-of-concept technique, history-sniffing attacks, and website fingerprinting attacks. The researchers targeted the latest versions of Chrome and Safari web browsers, with all side-channel protections enabled and standard “user” access privileges.
The attacks could discern the color of the pixels displayed on the target’s screen through CPU frequency leakage. They achieve this by employing Scalable Vector Graphics (SVG) filters to induce data-dependent execution on the target CPU or GPU, then using JavaScript to measure the computation time and frequency to infer the pixel color.
The accuracy of these measurements ranges between 60% and 94%, while the time required to identify each pixel varies between 8.1 and 22.4 seconds. The AMD Radeon RX 6600 GPU appears to be the most vulnerable device to “Hot Pixels” attacks, while Apple SoCs (M1, M2) seem to be the most secure.
In Safari, which restricts cookie transmission on iframe elements that don’t share the same origin as the parent page, researchers had to employ more creative strategies. Apple’s browser is susceptible to a sub-type of the “Hot Pixels” attack, which can infringe on the user’s privacy by extracting browsing history. In this case, the SVG filtering technique is used to detect the differing color of a previously visited URL, achieving a higher level of accuracy ranging from 88.8% (MacBook Air M1) to 99.3% (iPhone 13).
The researchers have already reported the “Hot Pixels” issue to Intel, AMD, Nvidia, and other affected companies. However, an effective countermeasure against this new and complex type of side-channel attacks does not exist yet. Users need not be overly concerned for the time being, as the current speed limit for data exfiltration is a mere 0.1 bits per second, even though this could be “optimized” with further research.
[ad_2]