
[ad_1]
A hot potato: Gamers looking to download cheats and cracks should beware of links in YouTube video descriptions. Hackers may have compromised the channels hosting the videos, turning them into vectors for spreading malware that can steal login credentials.
A new report from Kaspersky describes a malware campaign targeting gamers through YouTube. The malware can steal various kinds of credentials from a victim’s system, then use them to trick more users. In March 2020, Kaspersky discovered a trojan that bundles together multiple malicious programs that hackers used to spread through spam e-mails or third-party loaders.
Once activated, the payload also known as RedLine can steal data from Chrome, Firefox and Chromium-based browsers, including autofill information, usernames, passwords, cookies, and banking credentials. It could also steal information from crypto wallets, instant messaging software, FTP, SSH, and VPN clients. Furthermore, the malware could open links in the system’s default browser to download and open programs.
From there, the malware can propagate using an even more elaborate scheme. It downloads videos onto a victim’s machine advertising cheats and cracks for many popular PC games, then uploading them to the victim’s YouTube channel. The descriptions for the uploaded videos contain links purporting to lead to the advertised hacks, but instead, they lead to the trojan that uploaded the videos.
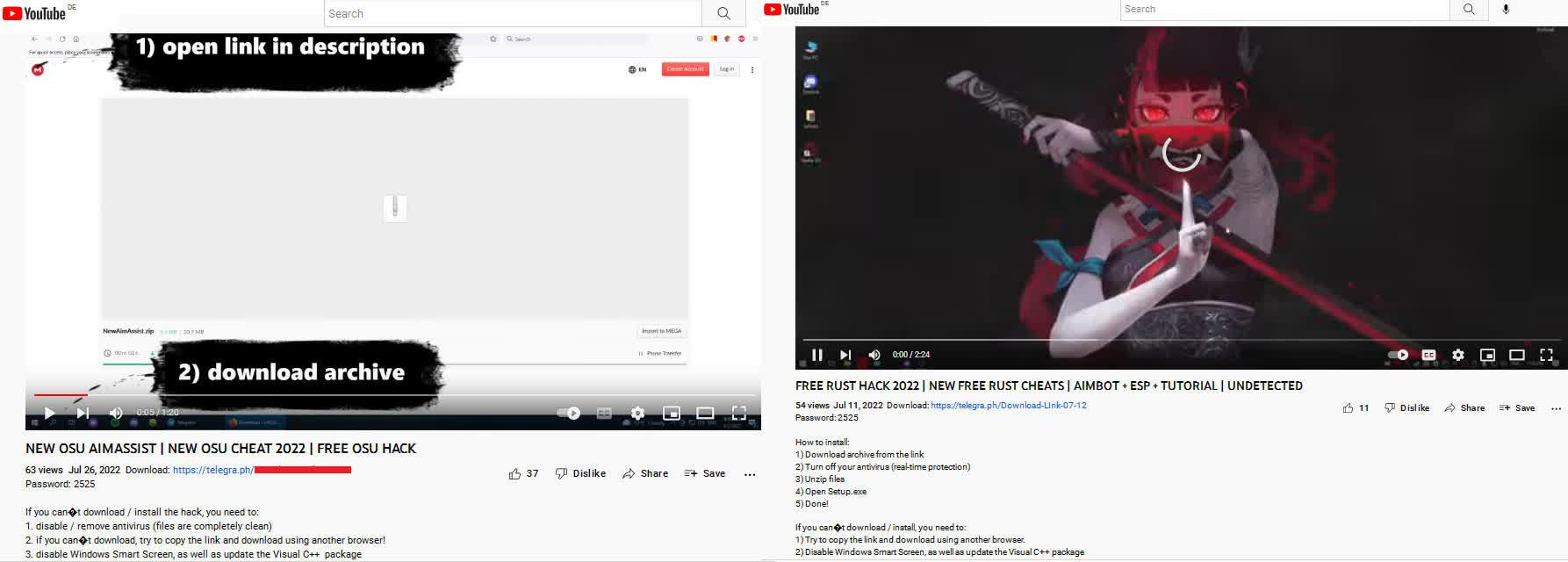
The videos mention games including Final Fantasy XIV, Forza, Lego Star Wars, Rust, Spider-Man, Stray, VRChat, DayZ, F1 22, Farming Simulator, and more.
YouTube has already shut down the compromised channels, but users should watch out for suspicious links on the site in case this propagation method becomes more popular in the future.
The payload also contains crypto mining software. Gamers are more likely to have powerful GPUs installed which can mine crypto. Fortunately, after this year’s crypto crash and Ethereum’s “merge,” it’s far less likely that hackers will continue to seek graphics cards to mine since it’s become less profitable, so perhaps this may become one less security threat to worry about.
Users looking to actively defend against this malware, or who think they may already have been targeted, should know that the RedLine trojan contains files named as follows: Makisekurisu.exe, cool.exe, AutoRun.exe, download.exe, and upload.exe. AutoRun copies itself into the directory %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup, causing it to run every time Windows starts.
[ad_2]