
[ad_1]
Why it matters: Hackers have been exploiting vulnerable drivers for years, and Microsoft can’t easily fix the underlying issue without angering some of its paying customers who are using older software. Over the past few years, a Windows policy loophole allowed malicious actors to sign and load so-called cross-signed kernel-mode drivers and distribute malware to millions of Windows PCs. The offending drivers have been blocked, but the policy remains unchanged.
If you practice good digital hygiene, you’re likely installing Windows updates soon after their release date, especially when they’re security-focused. However, hackers are constantly poking and prodding the security of Microsoft’s operating system and devising new ways to bypass any of the restrictions in place.
In a security advisory released this week, the Redmond giant details a major issue where no fewer than 133 drivers that were officially signed by its engineers had recently been used by malicious actors to distribute malware, which seems to be a recurring problem. The campaign in question has been primarily targeted at Chinese-speaking Windows users, but, given the method used, there’s a good reason to believe this has been used to target users around the world.
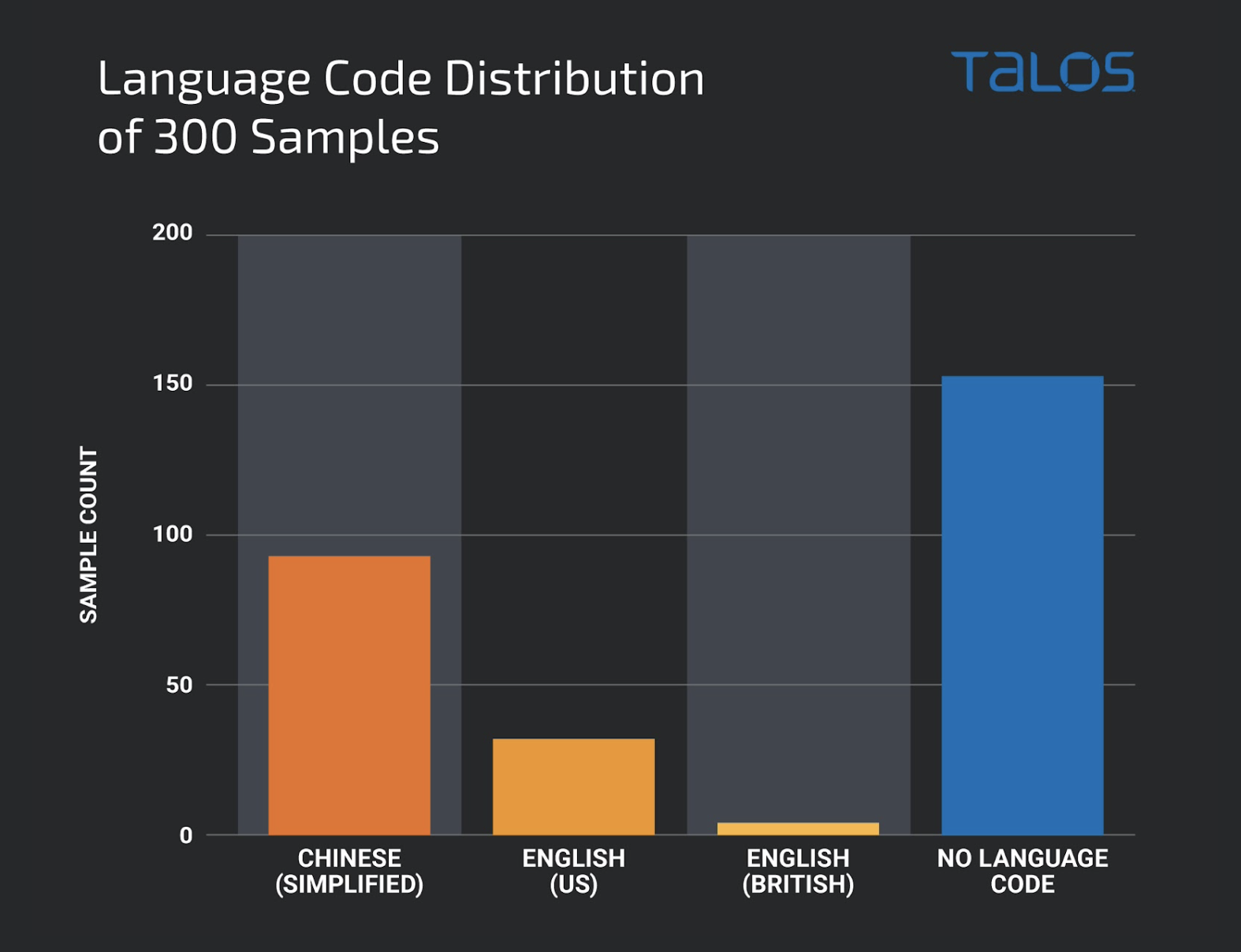
As explained by Cisco’s Talos security team, hackers found a Windows policy loophole that allowed them to load drivers signed before July 29, 2015. By using open-source tools such as HookSignTool and FuckCertVerifyTimeValidity, they were then able to compile new drivers and sign them using code-signing certificates from old drivers. As a result, they were able to install and load malicious drivers on pretty much any system.
The policy that makes all this possible is meant to allow compatibility with older software by allowing them to load older drivers in Windows 10 and Windows 11 without the need for them to be reviewed by Microsoft for safety implications. As for the open-source tools involved in the exploit, they’re very popular among game cheat developers who want to get their software to operate in kernel space or digital pirates looking to bypass DRM checks on popular apps and games.
The good news is that Microsoft has blocked the offending drivers as well as the accounts of the developers who wrote them. If you’re using Microsoft Defender (formerly known as Windows Defender) and have it up to date, a simple offline scan will detect if there are any malicious drivers in your system. The latest Patch Tuesday updates also include a revocation list that will prevent Windows from loading those drivers.
However, this approach of blocking malicious drivers once they’ve been reported by security researchers isn’t ideal since hackers typically get away with doing so for years before their code is blocked and Microsoft isn’t doing anything to close the loophole that made these exploits possible in the first place. Admittedly, one of the biggest selling points of Windows is the backward compatibility with older software, so the Redmond giant won’t have an easy time finding a better solution.
Masthead credit: Nahel Abdul Hadi
[ad_2]