
[ad_1]
Why it matters: Secure Boot is a technology designed to protect the PC boot chain and avoid running a tampered operating system. A firmware update released by MSI, however, changed the feature settings so that any OS image could run regardless of its legitimacy.
According to a young security researcher, MSI last year released a firmware update which made many of its motherboards less secure than they should have been.
First discovered by Dawid Potocki, a “student interested in FOSS and technology,” the issue concerns the Secure Boot feature on a significant number of MSI motherboards. Secure Boot is designed to make sure that a device boots using only software that is trusted by the OEM manufacturer, Microsoft explains.
When the PC starts, the firmware checks the signature of each piece of boot software (UEFI firmware drivers, EFI applications, the operating system). If the signatures are valid, the PC boots and the firmware gives control back to the operating system.
To work as intended, Secure Boot must be enabled and configured in a way that the booting process will accept operating systems with valid signatures only. Starting with a firmware update introduced at the beginning of 2022, Potocki discovered, MSI decided to change the Secure Boot default configuration to “accepting every OS image I gave it, no matter if it was trusted or not.”
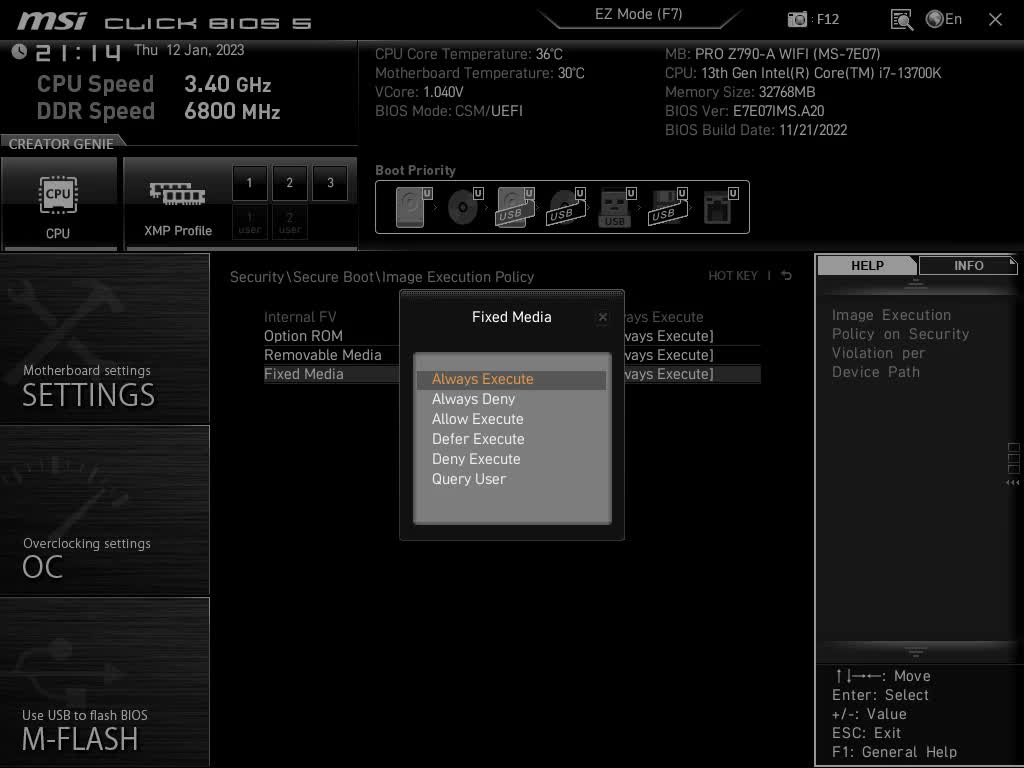
Potocki says he discovered the issue while setting up Secure Boot on his new desktop PC with the help of sbctl. He self-signed the Secure Boot process, but the UEFI firmware was booting every OS regardless of the signature. The firmware update changed a Secure Boot setting named “Image Execution Policy,” which was set to “Always Execute” rather than “Deny Execute” as it should have been.
With no signature verification and enforcing, Secure Boot is essentially useless even when it’s enabled. Potocki was able to trace the insecure default settings to firmware version 7C02v3C, an update released by MSI for the B450 TOMAHAWK MAX motherboard on January 18, 2022. The total number of affected motherboards is over 290, both for Intel and AMD processors.
Even though Secure Boot can be made effective again by just changing the Image Execution Policy options to “Deny Execute,” MSI has yet to issue a statement about the reason for turning off an important security feature for a large number of consumer motherboards.
[ad_2]