[ad_1]
Why it matters: You’re probably familiar with TP-Link’s Tapo smart bulbs. They’re incredibly popular, especially on Amazon, and the companion app has over 10 million downloads on Google Play. But researchers have discovered four vulnerabilities in a specific model of bulb and the Tapo app that could allow attackers to steal Wi-Fi passwords, among other things.
As reported by Bleeping Computer, researchers from Universita di Catania and the University of London wrote in a paper that IoT products are becoming increasingly pervasive. As such, they wanted to conduct a vulnerability assessment and penetration testing session on the Tapo L530E, currently the best-selling smart bulb on Amazon Italy.
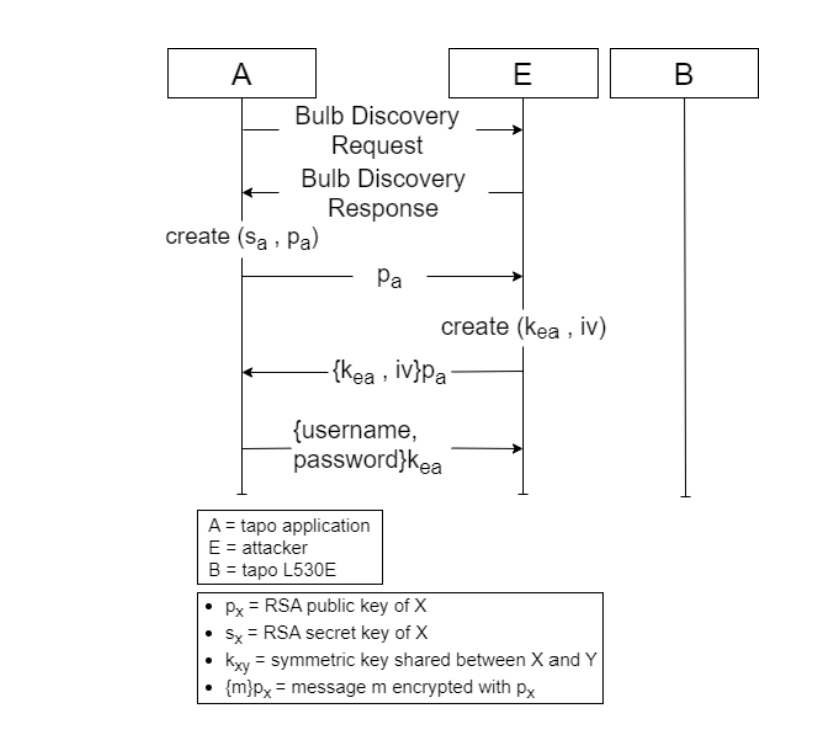
The results were not good for TP-Link. Researchers found four vulnerabilities, the first of which was calculated as having the highest CVSS v3.1 vulnerability score: 8.8, making it high severity. It’s due to a lack of smart bulb authentication with the Tapo app, allowing attackers to impersonate the bulb during the session key exchange step.
The vulnerability, present in all Tapo smart devices that use the TSKEP protocol, allows hackers to retrieve Tapo user passwords and manipulate Tapo devices.
The second flaw is also classed as high severity (7.6 score) and stems from a hard-coded short checksum shared secret. This lets an adjacent attacker obtain the secret used for authentication during the Bulb Discovery phase via a brute-force attack or by decompiling the Tapo app.
The third security issue (4.6 score) is a lack of randomness during symmetric encryption that enables an attacker to make the cryptographic scheme predictable.
The final vulnerability (5.7 score) relates to insufficient message freshness, which keeps session keys valid for 24 hours and allows attackers to replay messages during that period.
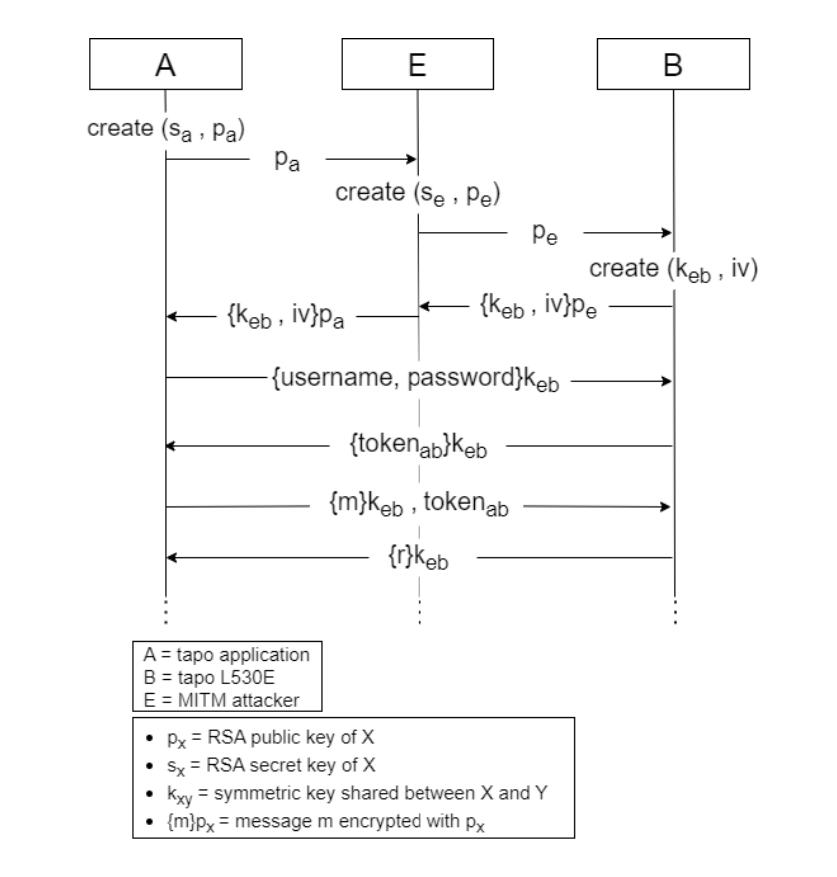
There are several scenarios in which someone could exploit the vulnerabilities, the most serious being bulb impersonation and retrieval of Tapo user account details. This could allow an attacker access to the Tapo app and, among other things, steal a user’s Wi-Fi password. While the device needs to be in setup mode for the attack to work, the attacker can repeatedly deauthenticate a bulb, forcing a user to run the setup again.
The researchers also warned of Man-In-The-Middle attacks with a configured and unconfigured Tapo L530E device, letting attackers intercept communications and retrieve Tapo passwords, SSIDs, and Wi-Fi passwords.
The good news is that the vulnerabilities have been reported to TP-Link via its Vulnerability Research Program (VRP). The company acknowledged all of them and said it has started working on fixes both at the app and at the bulb firmware levels. No word on when they will get here beyond their release “in due course.”
[ad_2]