[ad_1]
Recently Microsoft entered the world of managed detection and response (MDR) solutions with its “Microsoft Defender Experts for XDR”. An addition to Microsoft’s ever-growing security portfolio and one many of its customers may find attractive.
With this launch in mind, I thought it was a good time to revisit some research that I did here at GigaOm earlier this year, looking at MDR solutions, what they are and what they could do for you (Subscribers can click on these links to access the Key Criteria and Radar report).
MDR is a rapidly moving space whose development speed is driven by demand. Organizations of all types struggle to effectively tackle the ever-increasing and evolving security challenge, whether that is because of a lack of resources, skills or technology; there is a significant gap to fill, and in many cases, Microsoft and numerous others have realized that MDR may fill it.
What is XDR?
At a high level, MDR is a service that delivers management to XDR platforms. Why do they need managing? That’s a good question. Let’s start with an overview of what XDR is.
XDR (eXtended detection and response) platforms aggregate broad security threat telemetry from areas such as endpoints, networks, cloud apps and identity platforms into a single platform. Then, using a mix of analytics and threat intelligence information, the platforms will make automated judgements on the potential threat and mitigation steps required to keep an organization safe. These are powerful solutions that will improve an organization’s security posture.
XDR platforms are intelligent and automate many security and mitigation processes. But they are still tools that need the resources and skills to manage them. In conversations with C-suite execs, this is something I hear a lot. They have invested in technology platforms they are very happy with but need the internal resources to manage them. This raises questions about how to continue to use them effectively.
This is where MDR comes in—providing a human management wrap to an XDR platform. Usually, this is done via a mix of analytics and automation tools, crucially overseen by well-staffed, highly skilled teams of SOC analysts reviewing the platform and carrying out remediation tasks as needed.
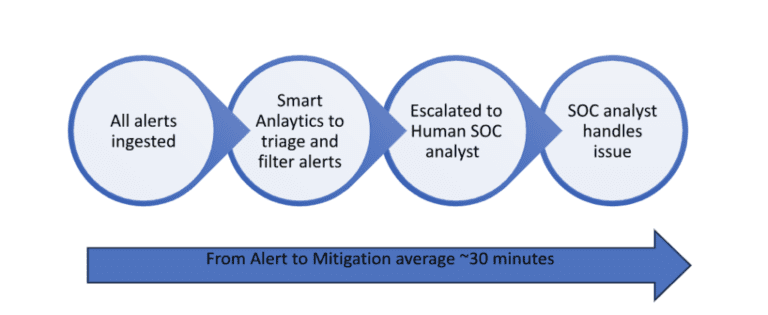
The MDR approach usually consists of using ML and Analytics to filter through millions of data points to filter out false positives and low-level issues, leaving just key incidents that require review. These incidents are presented to a SOC analyst who will add human insight and make a call on whether this is a priority incident or not. Then, depending on the agreement with the MDR provider, they will carry out that mitigation or alert customers of actions to be taken.

This is a hugely efficient mix of technology and human interaction, and importantly provides a very rapid “alert-to-fix” capability with leaders in the space claiming average times of in the region of 30 minutes, compared to a reported industry average of 16 hours for an internal SOC team, and in an area where speed of response is so critical, this alone can make a strong case to consider MDRs.
But I don’t want to throw everything away!
This all sounds great, but if you’ve got an investment in security tools, you’re not going to want to throw that away. That’s part of the benefit of how the MDR space is developing. Today, leading MDR vendors are not pushing “our agent everywhere” approaches. Instead, they have realized the importance of integrating with existing enterprise technology. Rather, it’s about integrating with that tech, using that to feed its platform and then using its intelligence and SOC analysts to qualify risk and apply mitigation steps. This can have downsides, especially around the automation of threat mitigation steps, but it does allow existing investments to be augmented with skilled SOC teams, which can add additional value to those existing investments.
Who are the MDR players?
There are two main types of MDR solutions; Vendors adding management to existing XDR, such as Microsoft, Sophos, CrowdStrike, Palo Alto and Sentinel One, and those building an MDR service with no requirement to use their technology, the likes of Artic Wolf, Expel and Deepwatch. From a customer point of view, there is no right or wrong approach to this market. It is just understanding what fits.
Is MDR for me?
The title of this piece is about whether MDR is something you should try out. Should you? In our initial MDR research, I highlighted some questions organizations should ask themselves to ascertain whether managed security is right for them. Those questions remain valid and ask whether your organization has the skills and resources to:
- Continually understand evolving threats?
- Monitor security to the extent that is needed?
- React in a timely manner to threats?
- Deal with a complex cybersecurity incident in a timely manner?
- Recover from a security incident effectively?
If the answer to any of these questions is no, then it is probably time to evaluate the MDR market and see if a vendor can help you fill those security gaps in a commercially effective way.
The cybersecurity threat landscape will only continue to become more complex and resource hungry for organizations. The ability to find the resources, skills and technology to deal with threats quickly will be increasingly difficult. MDR can be a very effective tool to help, so it may well be time to take a look!
The post As Microsoft joins the party, is it time to try MDR? appeared first on GigaOm.
[ad_2]