
[ad_1]
What just happened? Introduced in 2015, HTTP/2 brought several enhancements to the HTTP protocol including efficient data transmission, request handling, responsiveness, and header compression for website-based information transactions. But in addition to those efficiencies, HTTP/2 also brought its own unique set of challenges for administrators and security teams. Earlier this week, researchers announced a newly discovered HTTP/2-related exploit that can be used to conduct denial-of-service (DoS) attacks against vulnerable targets.
In a report from The Hacker News, security researcher Bartek Nowotarski was credited with reporting the issue to Carnegie Mellon’s Computer Emergency Response Team (CERT) Coordination Center on January 25.
The vulnerability, known as HTTP/2 CONTINUATION Flood, exploits improperly configured HTTP/2 implementations that fail to limit or sanitize the CONTINUATION frames in a requests’ data stream.
New HTTP/2 #vulnerability discovered.
“CONTINUATION Flood” attacks can lead to denial-of-service (DoS). This could cause crashes and serious website disruptions.
Find details here: https://t.co/mA2FrvgYNm#cybersecurity #technews #infosec
– The Hacker News (@TheHackersNews) April 4, 2024
CONTINUATION frames are a method used to continue a sequence of header block fragments, allowing header blocks to be split across multiple frames. The previously-fragmented header block is considered completed when the server receives a specific END_HEADERS flag, indicating that there are no further CONTINUATION or other frames.
HTTP/2 implementations are vulnerable to attack when the implementation does not limit the amount of CONTINUATION frames that can be sent within a single data stream. Should an attacker begin an HTTP request to a vulnerable server with no set END_HEADERS flags, the request would allow the attacker to send an ongoing stream of CONTINUATION frames to that server, eventually causing an out-of-memory crash and resulting in a successful denial of service (DoS) attack.
CERT also cited another variation of the vulnerability that uses HPACK Huffman encoded CONTINUATION frames cause CPU resource exhaustion, also resulting in a successful DoS attack.
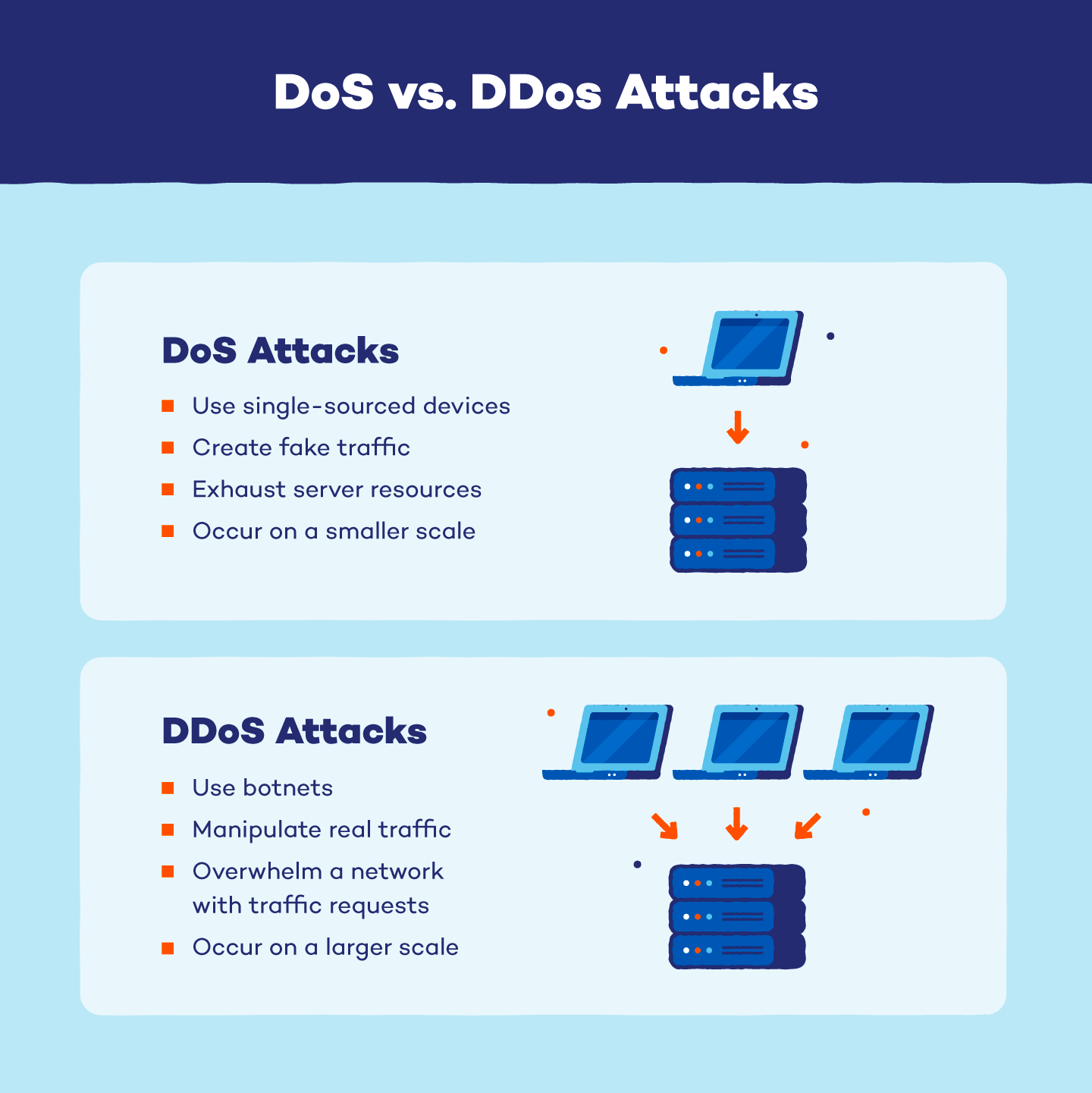
According to Nowotarski, a single machine or even a single connection has the potential to disrupt server availability, with consequences ranging from crashes to performance degradation.
Unlike a distributed denial of service (DDoS) attack that creates large scale botnets to overwhelm networks through sheer traffic volume, a DoS attack can create fake web traffic using a single device by flooding a transmission control protocol (TCP) connection with requests designed to exhaust a target server’s resources.
Several Common Vulnerability and Exposure (CVE) records have been created related to the new vulnerability. These include:
- CVE-2024-2653 – amphp/http
- CVE-2024-27316 – Apache HTTP Server: HTTP/2 DoS by memory exhaustion on endless continuation frames
- CVE-2024-24549 – Apache Tomcat: HTTP/2 header handling DoS
- CVE-2024-31309 – Resource exhaustion in Apache Traffic Server
- CVE-2024-27919 – HTTP/2: memory exhaustion due to CONTINUATION frame flood
- CVE-2024-30255) – HTTP/2: CPU exhaustion due to CONTINUATION frame flood
- CVE-2023-45288 – HTTP/2 CONTINUATION flood in net/http
- CVE-2024-28182 – Reading unbounded number of HTTP/2 CONTINUATION frames to cause excessive CPU usage
- CVE-2024-27983 – node::http2::Http2Session::~Http2Session() leads to HTTP/2 server crash
- CVE-2024-2758 – Tempesta FW rate limits are not enabled by default
According to a survey from w3techs.com, HTTP/2 is currently used by approximately 35.5% of all websites.
Administrators of affected servers should upgrade any software identified in the CVEs to the latest version in order to mitigate potential CONTINUATION threats. If a fix is not available, administrators are advised to consider temporarily disabling HTTP/2 on the impacted servers.
Image credit: Elchinator
[ad_2]