
[ad_1]
In brief: Several HP enterprise devices are running firmware containing as many as six unpatched security holes that allow arbitrary code execution. Some of them are at least a year old, and researchers publicly disclosed all of them over a month ago. As of this writing, all remain unpatched.
At the Black Hat 2022 conference last month, enterprise security firm Binarly disclosed six tracked vulnerabilities in several HP product lines, including EliteBooks. In a blog post last week, it shared the details to the wider public.
All the weaknesses involved a System Management Mode (SMM) memory corruption that opens the window for arbitrary code execution. These vulnerabilities allow an attacker to implant malware in a device’s firmware so that it can persist even after a fresh install of the operating system. This persistence is why the holes register as high threats.
“The impact of targeting unprivileged non-SMM DXE runtime drivers or applications by a threat actor is often underestimated,” said Binarly. “This kind of malicious DXE driver can bypass Secure Boot and influence further boot stages.”
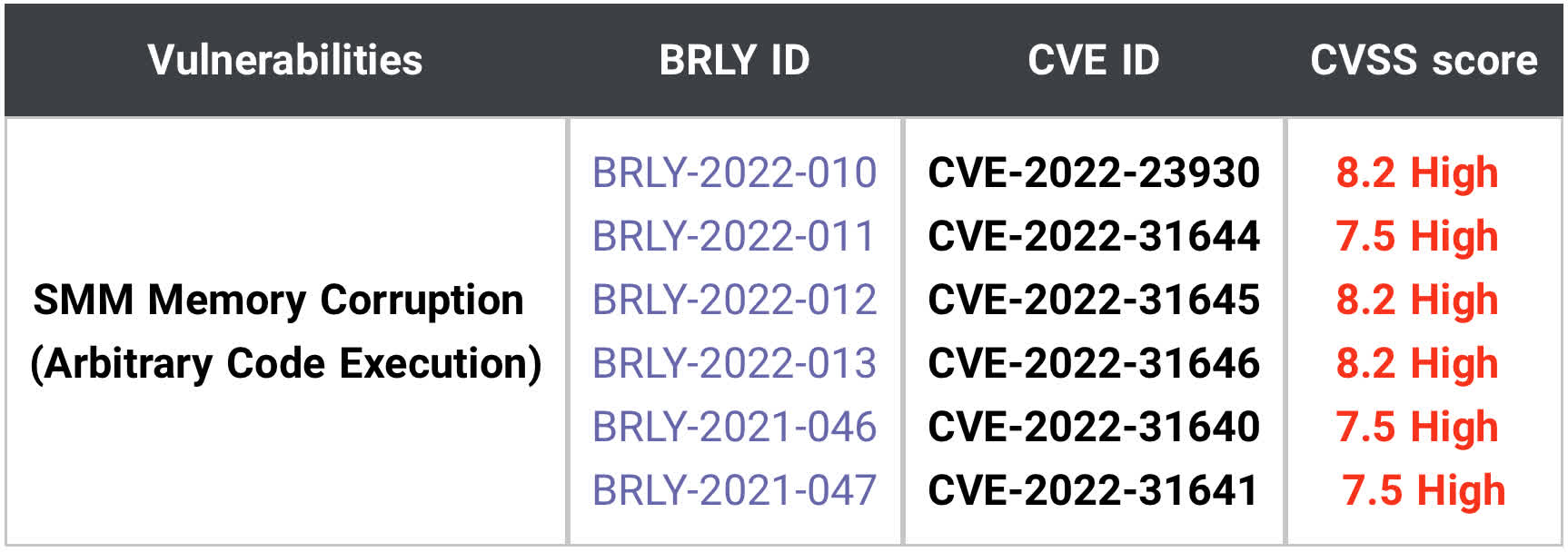
The six vulnerabilities were among 16 high-severity threats that Binary disclosed at the conference. Developers at HP patched 10 of them, but the remaining are still wide open. Whatsmore, the bugs are not new. Researchers discovered three in July 2021 and three in April of this year.
Half the flaws allow buffer overflows because of inappropriate handling of pointers in the CommBuffer. Checks to verify that the buffer is within an expected range are missing. Two others exist because of improper input validation. Binarly says this oversight allows attackers to gain control of the CommBuffer and modify it. The last vulnerability is caused by a lack of sanitation in the CommBuffer. Attackers with control of the buffer can create a stack-based overflow leading to an opportunity for arbitrary code execution in SMM.
“Unfortunately, at the time of writing, some HP enterprise devices (laptops and desktops) have still not received updates to patch the aforementioned vulnerabilities, despite them being publicly disclosed for over a month,” Binarly notes.
Researchers privately reported all the flaws to HP as they discovered them, but they remained unpatched. So Binarly used Black Hat 2022 to disclose and discuss the weaknesses to warn enterprise admins of the threats.
Since these vulnerabilities are at the firmware level, full mitigation can only come from HP. However, Binarly has software available on GitHub called FwHunt that can identify if the threats exist in a company’s infrastructure. Detection will at least allow administrators to isolate and possibly contain vulnerable machines.
[ad_2]