[ad_1]
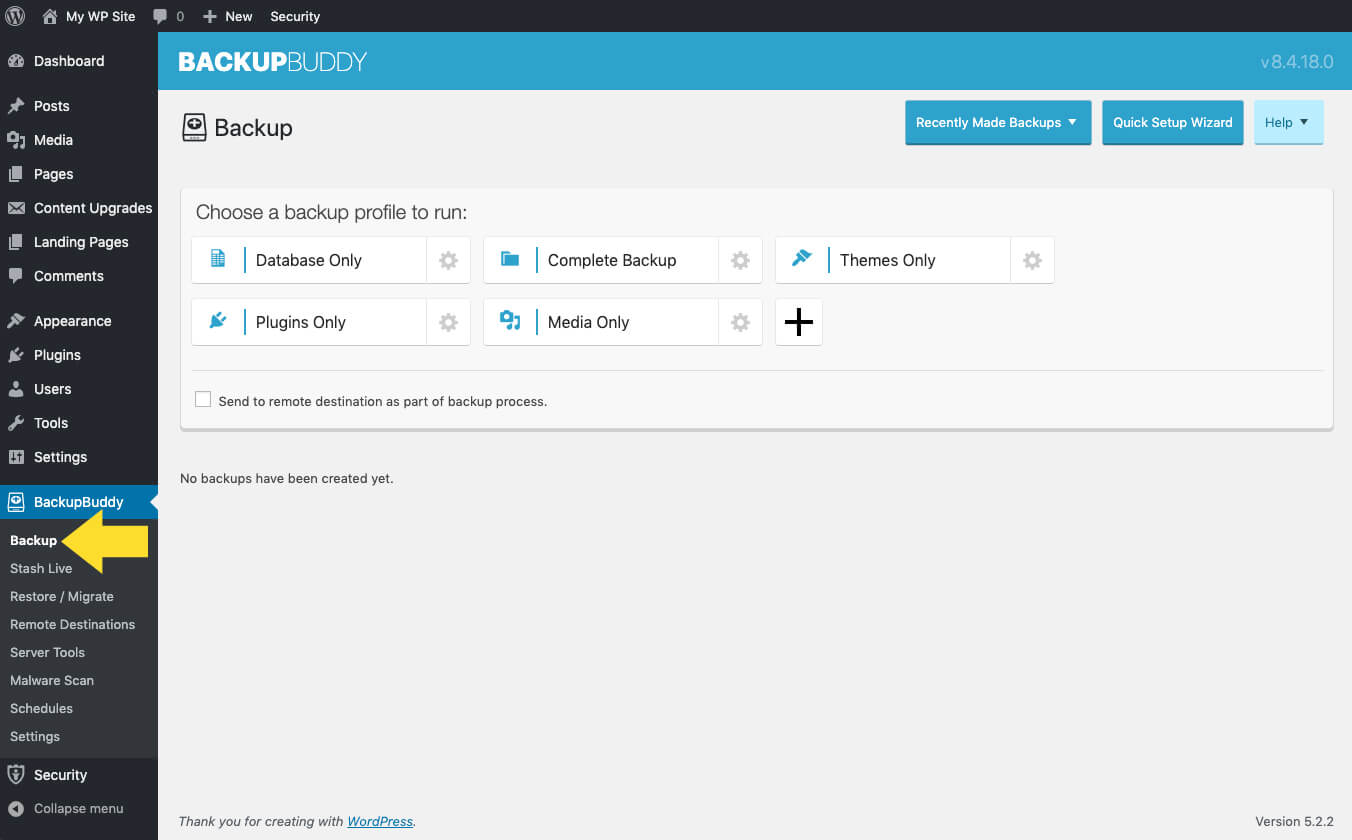
Why it issues: WordPress plugin developer, iThemes, alerted customers to a vulnerability associated to their BackupBuddy extension earlier this week. The safety gap leaves plugin customers vulnerable to unauthorized entry by malicious actors, offering them with the chance to steal delicate recordsdata and knowledge. The flaw impacts any websites working BackupBuddy 8.5.8.0 by 8.7.4.1. Customers ought to replace to model 8.7.5 to patch the outlet.
Based on iThemes researchers, Hackers are actively exploiting the vulnerability (CVE-2022-31474) throughout impacted techniques utilizing particular variations of the BackupBuddy plugin. The exploit permits attackers to view the contents of any WordPress-accessible file on the affected server. This contains these with delicate data, together with /and so forth/passwd, /wp-config.php, .my.cnf, and .accesshash. These recordsdata can present unauthorized entry to system consumer particulars, WordPress database settings, and even authentication permissions to the affected server as the foundation consumer.
Directors and different customers can take steps to find out if their web site was compromised. Approved customers can evaluate an impacted server’s logs containing local-destination-id and /and so forth/handed or wp-config.php that return an HTTP 2xx response code, indicating a profitable response was acquired.
WordPress safety answer developer Wordfence recognized thousands and thousands of makes an attempt to use the vulnerability courting again to August twenty sixth. Based on Wordfence safety researchers, customers and directors ought to examine server logs for references to the aforementioned local-destination-id folder and the local-download folder. The PSA went on to checklist the highest IPs related to the tried assaults, which embrace:
- 195.178.120.89 with 1,960,065 assaults blocked
- 51.142.90.255 with 482,604 assaults blocked
- 51.142.185.212 with 366,770 assaults blocked
- 52.229.102.181 with 344,604 assaults blocked
- 20.10.168.93 with 341,309 assaults blocked
- 20.91.192.253 with 320,187 assaults blocked
- 23.100.57.101 with 303,844 assaults blocked
- 20.38.8.68 with 302,136 assaults blocked
- 20.229.10.195 with 277,545 assaults blocked
- 20.108.248.76 with 211,924 assaults blocked
Researchers at iTheme present compromised BackupBuddy customers with a number of steps designed to mitigate and stop additional unauthorized entry. These steps embrace resetting WordPress database passwords, altering WordPress salts, updating API keys saved within the wp-config.php file, and updating SSH passwords and keys. Prospects requiring extra assist can submit assist tickets by way of the iThemes Assist Desk.
Picture credit score: Justin Morgan
[ad_2]